Creating security rules
Security rules enabled administrators to control what information each user, security group, or workstation/computer can access, and what actions they can perform in Wolf EMR. For example, you can:
Restrict specific users, members of a specific security group, or users on a specific workstation from performing certain actions or viewing certain information in Wolf EMR.
Enable specific users, members of a specific security group, or users on a specific workstation to perform an action or view information that is restricted to them by default based on their role.
Restrict specific patient records from displaying on the patient portal.
Note: User-specific security rules override group security rules. Computer/workstation or IP address-specific rules override both user-specific and group security rules.
Only users with the administrator authority can assign security rules to users and roles.
Steps
| 1. | From the Wolf EMR home page, click Configuration |
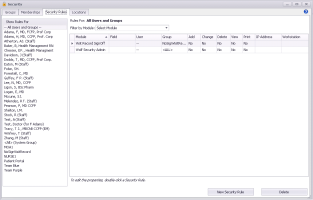
| 2. | From the Configuration menu, choose View > Security > Security Rules. The Security window opens with the Security Rules tab selected by default. |
A list of clinic users and security groups appears on the left.
A list of security rules that were created appears on the right.
Tip: If the list of rules is long, use the Filter by Module field to filter the list. Or, click a column header to change the sort order.
| 3. | Click the user or group for which you want to create or edit a security rule. |
| 4. | To create a new security rule, click New Security Rule. |
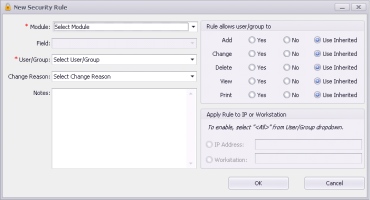
The New Security Rule window opens. Use the following table to create the rule.
| Field | Description |
|---|---|
|
Module |
Select the Wolf EMR feature or area to which you want to restrict or enable access or action privileges. |
|
Field |
If the module you chose has specific fields or items, select it. Otherwise, this field is greyed out. |
|
User/Group |
Select the user or group to which the security rules apply. Security groups appear below user names. To apply the rule to all users, choose <All> (System Group). To apply the rule to a specific computer (instead of a user or group), click <All> (System Group). You must then also specify details in the Apply Rule to IP or Workstation area. |
|
Change Reason |
Select the reason for creating the security rule. If the reason you want is not available, click Other, and then type the reason in the Notes area. |
|
Rule Allows user/group to |
Select the permissions to give for each action privilege (Add, Change, Delete, View, and Print): Yes: To enable the user or group to perform this action. No: To restrict the user or group from performing this action. Use Inherited: To use inherited permissions based on the user’s role or group. |
|
Apply Rule to IP or Workstation |
To apply this security rule to a specific computer (instead of a user or group), complete one of the following actions: To select a computer/workstation based on its IP address, click IP Address and enter the IP address. To select a computer/workstation based on its network name, click Workstation and enter the computer’s network name. |
| 5. | To edit a security rule, double-click a rule and use the table above to edit the rule. |
| 6. | To delete a security rule, select it and click Delete. |
| 7. | When you are done, click Close |
© 2018